We spend our days looking forward forecasting new threats and ...
Don't Get Phished
-
By Loïc Calvez

Let’s start at the beginning: What is phishing?
Wikipedia provides us with a good starting point:
“Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit card details by disguising oneself as a trustworthy entity in an electronic communication.”
Often in the form of an email (and more and more in the form of text messages (and soon to include a lot of instant messaging)), you get a communication telling you something or asking for something to trick you in providing a piece of data (directly or indirectly, more on that later).
You might be wandering: Why do cybercriminals use phishing? The quick answer: because it works!
It all comes down to money. Cybercrime is a USD$1.5 trillion industry (Bromium 2018, probably even more today) and for cybercriminals to make money, they need your data. By data we mean of course: Personally Identifiable Information (PII, who you are, name, address, social insurance number…) which when combined with credit card numbers becomes even more valuable, but it can also include financial results of a private company, secret formula, marketing plans… Anything that can be monetized by selling it to someone (another criminal or your competitor), withhold it from you (ransomware) or leak it to the public if you don’t pay the ransom (a variant of ransomware).
Here are some statistics to ponder about before we dive in:
- 94% of malware was delivered via email (Verizon Data Breach Investigations Report (DBIR) 2019)
- 87% of mobile phishing attacks take place outside an email (Wandera Threat Landscape 2020)
- Small businesses represented 43% of all data breaches (Verizon Data Breach Investigations Report (DBIR) 2019)
Once upon a time, phishing emails were very sad attempts targeted at the early breed of Internet dwellers that believed the Internet was meant for the greater good and could bear no evil. They were crude, contained obvious misspelling, logos were off colors or outdated. Today’s phishing communications are picture perfect copies of the real ones, but since the average Internet user is also [slightly] more careful, the new generation of phishing attacks is getting quite devious. A good example: you receive a message from Microsoft telling you that someone has attempted to reset your password and to click the link below to report it immediately if it was not you.
“The message did not come from Microsoft, nobody tried to reset your password, the link connects you with a malware payload to attempt to infect your computer and steal your data.”
So, putting ourselves in the mind of a cybercriminal, how do you create a good phish attack?
It needs to look real (easy), it needs to look like it is coming from a trusted source (bank, government, large tech company …), it needs to look inoffensive (no blatant: click here to download X) and the most important one, it needs to create a sense or emergency (your account will be suspended, you will need to pay some additional fees, the government will come for your assets).
Now that we know what the perfect phish looks like, we know what to look for. Here is another example (courtesy of Wandera) of a recent phish attack that has been circulating:
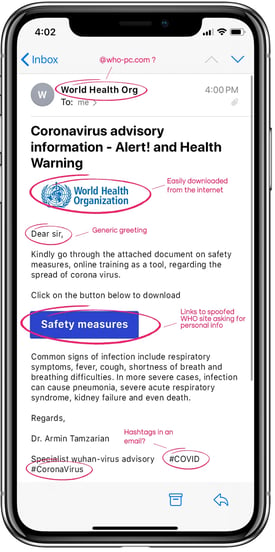
We can see that is has all the elements: it looks real, pretends to come from someone you can trust and tries to create a sense of urgency with the safety angle. So, how do you recognize it as a phish? If you look at the From: email address (the real address you see if you hover over it with your cursor, not the text they are showing you), you would see it was from @who-pc.com (the real one is @who.int), the greeting is generic and if you hover over the “Safety measures” link you would have seen that the link was quite scary looking (long with very unrelated domain names, be also mindful of very short ones from free URL shortener like bit.ly). The question you should now be asking is: how do I hover on mobile devices? Well, on most devices today, you can’t… So the answer is simple, don’t click. If you feel it might be real and urgent (like a message from your bank saying your account has been compromised), call (the number on the back of your card or on a public website, not the number in the email).
And this is where we see the most important weapon in your arsenal to fight phishing attacks: The Pause. Take a deep breath and question everything. Once you are satisfied that the email is what it pretends to be, then you can decide to take action. My recommendation would still be to not click on it if you can avoid it, just go to the actual website like you would normally do and login directly. It may take a couple of extra seconds, but it might save you from a world of hurt if you missed something.
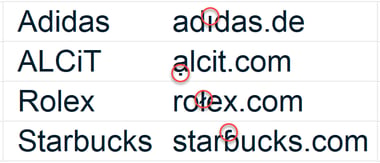
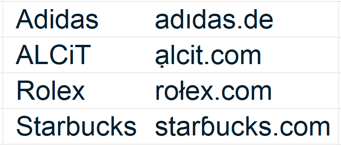
Before we get to best way for a business to protect itself, we wanted to bring your attention to an emerging kind of attack: the punycodes. They are a way to use the extended alphabet (letters with special accents, dots...) as part of URL. Why is this important? Because it is another way an attacker may trick in thinking you are clicking on a legitimate link, it has been used in Ad links (the ones at the top in Google searches for example) and of course in phishing attacks.
Here are some examples to help you see the difference:
So how does a business protect itself from phishing? A lot of it is similar to protecting you from other types of cyberattacks. From one of our latest blogs here, we identified these key defence strategies:
1. Train your people (attacks usually target humans first, not technology)
2. Patch everything (patches are updates from vendors to fix issues)
3. Deploy advanced email security to stop the new types of malware (94% of attacks start by an email)
4. Inspect all web traffic (including encrypted one) to detect the new types of malware (84% of web traffic is encrypted)
5. Deploy a next generation anti-malware on all devices (it’s your last line of defence)
6. Backup all your data to a place no one can delete it (physically and logically) and yes, you must backup Office 365 and G-Suite data
#1 should include general cybersecurity training, but we would also highly recommend adding phish training, this will train you and your employee to build that “muscle memory” of creating that pause moment before you click and help develop good habits, more details here.
#2 to #5 are more along the best practices, to secure you environment and will help protect you from the indirect parts of phishing attacks. Some attacks will directly try to get your login, password …, but other attacks will try to deploy malware to be exploited by the cybercriminal later (suck as data exfiltration or ransomware).
And #6 is your safety net, assuming all fails (you or one of your employees click on something they should not have (with devastating consequences)), you can still recover quickly with limited damages.
So quick recap:
- Take a pause
- Be skeptical
- Go directly to the source (do not click on that link)
And if you didn’t find the punycodes: (no dot on i, dot under a, different L and different B )