We spend our days looking forward forecasting new threats and ...
Creating a Cybersecurity Framework 1 of 5
-
By Loïc Calvez

In the spirit of the Cyber Security Awareness Month, we wanted to do a five part article on the Five Functions of NIST (National Institute of Standards and Technology). The goal is to provide a high-level overview of the things you should be doing to be more Cybersecure. We like the NIST framework because it is simple, logical and expandable. Everything you build as per the below would be rolled into your Cybersecurity program and enforced via policies.
The first function is “Identity”, the official definition: “The Identify Function assists in developing an organizational understanding of managing cybersecurity risk to systems, people, assets, data, and capabilities.” As we said: logical. If you want to protect yourself from cyber threats, you need to know what you need to protect! (and we will of course focus on data).
Step 1: Create a list of assets and people: all physical, logical and software assets in your organizations and the [groups of] people using them including, but not limited to:
- Physical: desktop, laptops, tablets, barcode guns, smartphones, smart TVs, digital signage, servers, firewall, switches, wireless access points, wireless bridges, wireless extenders, sensors, cameras, tokens,
- Logical: employee/customer/vendor information, access logs (building, computers, servers, camera system, folders, vpn), raw data (current and past test results, sensor data)
- Software: operating systems, office suite, pdf readers, text readers, ERP, graphics suite, analysis suites
Step 2: Establish a data classification framework and evaluate it against your different data (for example, public, private, confidential and secret)
Step 3: Looking at the assets in step 1 and evaluating it against the data sensitivity in step 2 start evaluating the actual risks, the main factors being:
- Destruction (loosing the actual data)
- Private dissemination of the data (your competitor getting your secret sauce)
- Public dissemination of the data (the public made aware of something you would have preferred to keep private)
- Integrity: someone modifying the data without your knowledge (changing the result of a test from fail to pass)
A risk is a combination of the likelihood (rare, unlikely, moderate, likely, almost certain) of something happening vs the impact (negligible, minor, moderate, major, severe) of that thing happening, based on the matrix below you can assign a risk from very low to extreme.
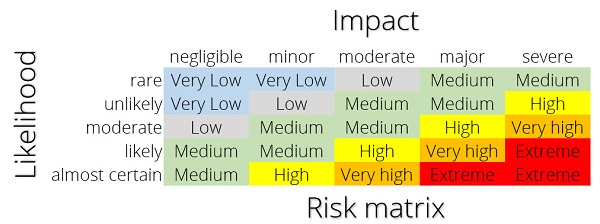
So for example: One of your executives has the entire finances of the company on his/her laptop (it is not encrypted, but it is backed up). According to our classification, that data would be typically be considered confidential, not secret. Evaluating against the risk above:
- Destruction: likelihood would be moderate (laptops are fragile), impact would be minor (you have backups, mostly time wasted restoring), therefore a medium risk
- Private dissemination: likelihood would be moderate (laptops get stolen often), impact would be major (you don’t want them to know that), therefore a high risk
- Public dissemination: likelihood would be moderate (laptops get stolen often), impact would be severe (lack of trust from public, possible fines), therefore a very high risk
- Integrity: likelihood would be unlikely (they would need access to the laptop without getting noticed) impact would be minor (information exists in other systems, but could lead to some bad decisions), therefore a low risk
(hint: with information like this, you can now make some good decisions, like in the above: just encrypting that laptop would eliminate the high and very high risks).
As you start getting Cybersecure, here is a list of documents you should be creating:
- Asset List with risk classification
- Acceptable Use Policy (AUP)
- Data Classification
- Cybersecurity Incident Response Plan
- Information Security Policy
- Change Management Policy
- Remote Access Policy
- Email/Communication Policy
We hope this will help to get you started on your Cybersecure journey. All documents and information are only made available for informational purposes, you should work with a professional to adapt them to your business.
Stay tuned for the next of the Five Functions: Protect.







